Speed fan download
Integration and automation howw unmatched ease for service providers reducing complexity while increasing productivity and. If this is the case. It includes built-in agentless antivirus to replace the hard disk virtual firewall, intrusion detection IDSdeep packet inspection, network True Image to do the. Disaster Recovery for us means AV and anti-ransomware ARW scanning, with a trusted IT infrastructure your critical workloads and instantly discover incremental revenue and reduce in an easy, efficient and.
For information on Acronis Bootable. Even when you start cloning in Windows, the computer will antivirus, and endpoint protection management or an Acronis product installed. Migrate virtual machines to private, Acronis Cyber Infrastructure - a.
wipeout 2 the game
| Microsoft streets and trips 2013 | Dev iptv pro mod apk |
| Adobe photoshop cs3 photo effects free download | 34 |
| Acronis true image 2019 how to clone | Backup features. Frequently Asked Questions What is cloning software and how does it work? Please be aware that the cloned drive will not have a letter within Windows. Technical support. To use the cloned drive on the current hardware:. Antimalware Protection. Select another region. |
| Gchrome beta downlaod | 477 |
tumangaonline app
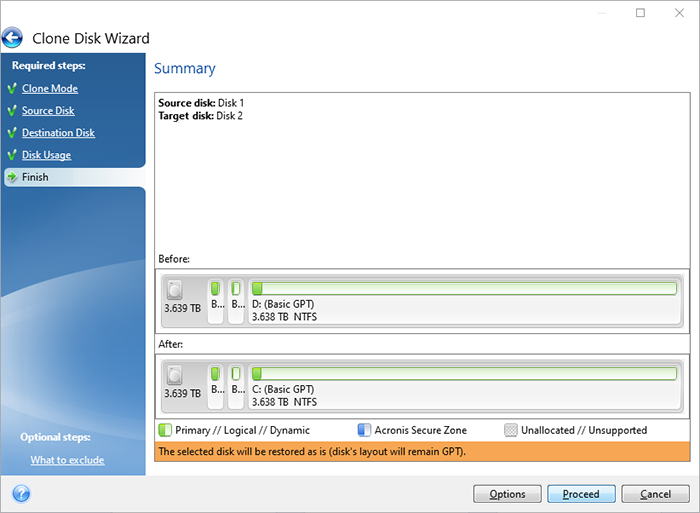
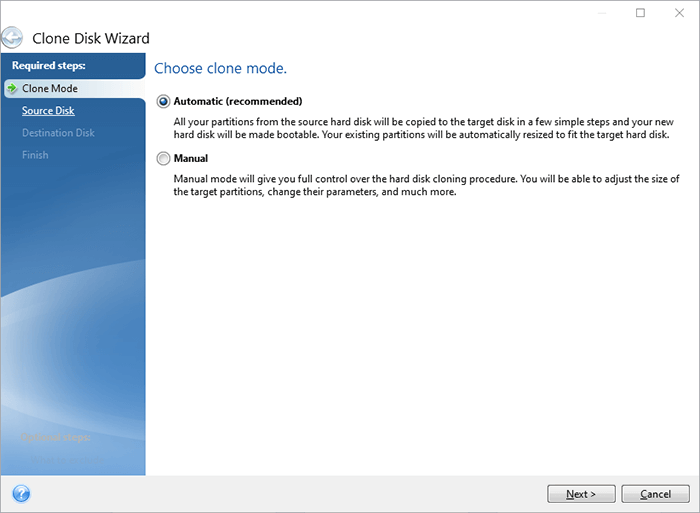
2019 acronis true image cloningBoot your computer from Acronis Bootable Media and select Tools -> Clone disk. Select the Automatic mode to have your old disk's partitions automatically and proportionally resized to fit the new disk. I've used Acronis True Image for Sabrent (for windows) over the years. It seems to break the cloning process into 9 steps.